Recovery metrics like RPO, RTO, WRT, and MTD form the foundation of effective disaster recovery and business continuity planning. These aren't just technical measurements—they're how business leaders define acceptable risk and guide cybersecurity investments that protect organizational resilience.
Understanding these four critical metrics is essential not only for passing the CISSP exam but also for your success as a cybersecurity professional. When you master these concepts and apply them in your planning, you demonstrate how security supports business goals—making it easier to secure the resources needed to protect your organization.
Watch the complete video explanation of disaster recovery metrics
Why Recovery Metrics Matter
Before diving into individual metrics, it's crucial to understand their strategic importance. Recovery metrics are the language through which security professionals communicate with business leaders. They translate technical recovery capabilities into business terms that executives understand—time and money.
When a security team can articulate that a critical system has an RTO of 2 hours and an RPO of 15 minutes, business leaders can make informed decisions about whether that level of protection aligns with their risk tolerance. Without these metrics, disaster recovery planning becomes guesswork, and organizations often discover gaps only during actual incidents—when it's too late.
Recovery metrics should be determined through collaboration between IT/security teams and business stakeholders. Technical capabilities mean nothing if they don't align with actual business requirements.
Understanding MTD (Maximum Tolerable Downtime)
MTD, or Maximum Tolerable Downtime, is arguably the most important metric and should be determined first in your planning process. It answers a fundamental question: "What is the absolute maximum amount of time a business process can be unavailable before causing severe or irreparable harm to the organization?"
This isn't a technical measurement—it's a business decision that considers financial impacts such as lost revenue and penalties, reputational damage, regulatory consequences, and customer impacts. MTD represents the point of no return, the threshold beyond which the organization faces unacceptable consequences.
MTD serves as the ultimate boundary for all your recovery planning. Every other metric—RTO, WRT, and RPO—must fit within this limit. Think of MTD as the "hard deadline" that your entire recovery strategy must respect.
Real-World MTD Examples
Consider an e-commerce platform that determines their MTD is 4 hours during business hours. Beyond that point, they'll lose customers permanently to competitors—the damage becomes irreparable because customer trust erodes and buying behavior shifts.
Contrast this with a hospital's electronic medical record (EMR) system, where the MTD might be just 20 minutes before patient care is severely compromised. When EMRs are unavailable, clinicians can't access critical patient information, delaying vital clinical decisions and treatment plans. This can quickly lead to life-threatening situations, regulatory violations, and significant liability.
Recovery Time Objective (RTO)
RTO is the maximum acceptable time to restore systems and applications after an incident. It answers the question: "How quickly must we get our systems back online?"
RTO starts at the moment of disruption and ends when your systems are restored and available. However—and this is crucial for the CISSP exam—"available" doesn't always mean "fully operational." Your database might be online, but is it accessible to users? Is all functionality restored?

This distinction is where WRT becomes essential—it bridges the gap between "available" and "fully operational." RTO measures the time until systems are running, while WRT accounts for the additional time until business can actually resume normal functions.
Different systems will have different RTOs based on their criticality. Your authentication servers might have an RTO of 1 hour, while the company blog might have an RTO of 24 hours or more. When setting RTOs, remember they must always be shorter than your MTD.
Work Recovery Time (WRT)
WRT, or Work Recovery Time, is one of the most frequently overlooked metrics in disaster recovery planning—and it's a favorite topic for exam questions because many candidates forget about it.
WRT is the time required after systems are restored to complete additional tasks necessary for full business functionality. It answers the question: "After systems are back online, how long until we're fully operational?"
Common WRT Activities
These post-recovery tasks might include data validation to ensure integrity, testing critical functions before releasing to users, manual data entry for transactions recorded during downtime, and notifying users that systems are operational. For example, after restoring a financial system, you might need an additional 2 hours to verify transaction integrity before allowing users back in.
RTO + WRT must be less than MTD. Your total recovery time cannot exceed what the business can tolerate. If your MTD is 5 hours, and your RTO is 4 hours, you only have 1 hour for WRT activities. Plan accordingly.
Recovery Point Objective (RPO)
While the previous metrics focused on time to recovery, RPO focuses on data loss. It answers the question: "How much data can we afford to lose?"
RPO is measured in time—15 minutes, 4 hours, 24 hours—and determines your backup frequency. An RPO of 1 hour means your backup strategy must ensure you never lose more than 1 hour's worth of data. The clock runs backward from the incident to your last good backup.

RPO Cost Considerations
For a hospital's electronic medical records, the RPO might be near-zero, requiring continuous replication—because losing even minutes of patient data could have life-threatening consequences. For a marketing analytics database, an RPO of 24 hours might be perfectly acceptable.
RPO has significant cost implications. The closer to zero your RPO gets, the more expensive your backup and replication infrastructure becomes. Expect exam questions that test your understanding of this cost-benefit tradeoff.
Putting It All Together: A Practical Example
The following scenario demonstrates how these concepts work together in practice—the kind of analysis required for both the CISSP exam and professional disaster recovery planning.
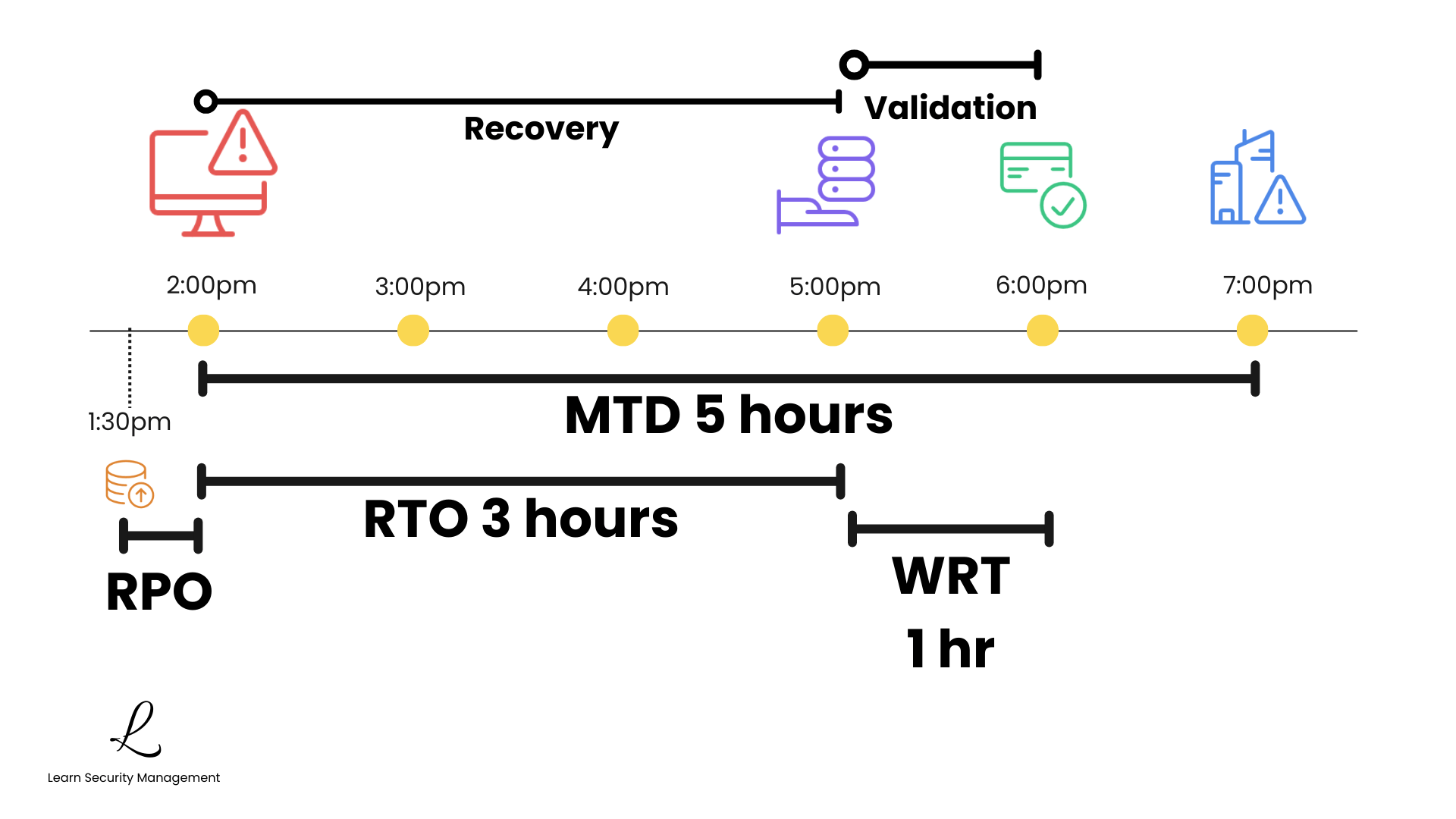
The Scenario: Ransomware Attack
Imagine a ransomware attack hits your organization at 2:00 PM on a Tuesday. Your organization has determined the MTD for your core business application is 5 hours. This means by 7:00 PM, you must be fully operational or face severe business consequences.
Your RPO is 30 minutes, so you have backups from 1:30 PM. This means you'll lose, at maximum, 30 minutes of data. Your team works to restore systems from backup, completing this by 5:00 PM—that's a 3-hour RTO.
After systems are restored, your team needs an additional hour to validate data integrity and ensure all connections are working. That's a 1-hour WRT.
The Math
Total downtime: RTO (3 hours) + WRT (1 hour) = 4 hours. Since your MTD is 5 hours, you've successfully recovered within your tolerance threshold. If your recovery had taken 6 hours, you would have exceeded MTD, potentially causing severe business impact.
Always build buffer time into your recovery plans. In this example, the 1-hour buffer between actual recovery (4 hours) and MTD (5 hours) provides margin for unexpected complications.
Implementation Tips for Security Professionals
The following best practices support effective implementation of recovery metrics—applicable to both exam scenarios and real-world security programs:
1. Start with MTD
Work with business leaders to determine the maximum tolerable downtime for each critical process. This should come first, as it establishes the boundary for all other metrics. Don't let IT drive this conversation alone—business impact is a business decision.
2. Be Realistic About RTO
Your RTO must account for all steps in the recovery process—from detection to restoration. Test your recovery processes regularly to verify your RTOs are achievable. Paper plans that haven't been tested are just assumptions.
3. Don't Forget WRT
Many recovery plans fail because they overlook the time needed after technical recovery. Document all post-recovery tasks and include them in your planning. This is where theory meets reality.
4. Balance RPO and Cost
Near-zero RPOs are technically possible but can be extremely expensive. Work with business stakeholders to find the right balance between data loss tolerance and cost. Sometimes accepting a slightly higher RPO dramatically reduces infrastructure costs.
5. Document Everything
Create clear documentation that lists your RTOs, RPOs, WRTs, and MTDs for all critical systems. This documentation is essential during certification audits and actual disaster scenarios. When a real incident occurs, you won't have time to figure out priorities.
Conclusion
Understanding these four metrics—MTD, RTO, WRT, and RPO—is fundamental to creating effective disaster recovery and business continuity plans. They form the foundation upon which you'll build your technical recovery strategies and communicate with business stakeholders.
Remember the key relationships: MTD is your absolute limit for downtime, RTO is your system restoration time, WRT is your post-restoration work time, and RPO is your data loss tolerance. Most importantly, RTO + WRT must be less than MTD, or your recovery plan won't meet business needs.
Mastering these recovery metrics is essential for cybersecurity professionals. Taking time to understand how they relate to one another and applying them to various scenarios builds the analytical foundation needed for certification exams like CISSP and for helping organizations build resilient systems throughout a security career.
Core Definitions
- MTD (Maximum Tolerable Downtime): Absolute maximum time a process can be unavailable before causing severe harm—determined by business, not IT
- RTO (Recovery Time Objective): Maximum acceptable time to restore systems after an incident—from disruption to system availability
- WRT (Work Recovery Time): Time required after system restoration to complete tasks for full business functionality
- RPO (Recovery Point Objective): Maximum acceptable data loss measured in time—determines backup frequency
Critical Relationships
- Formula: RTO + WRT must be less than MTD
- Sequence: RPO → Incident → RTO → WRT → MTD
- MTD comes first: Establishes the boundary for all other metrics
- RPO drives backup strategy: Lower RPO = more frequent backups = higher cost
Common WRT Activities
- Data validation: Verifying integrity of restored data
- Function testing: Testing critical functions before user access
- Manual data entry: Entering transactions recorded during downtime
- User notification: Communicating system availability
Exam Tips
- Remember: MTD is a business decision, not a technical one
- Common mistake: Forgetting WRT when calculating total recovery time
- Focus on: The cost implications of aggressive (near-zero) RPO targets
- Key distinction: RTO ends at system availability, not full business operations
Exam Focus: The Security Manager's Perspective
CISSP tests your ability to think like a security manager, not just a technician. Apply these metrics strategically.
- Business Impact Analysis (BIA) Integration: Recovery metrics don't exist in isolation. MTD emerges from BIA findings—the process that identifies critical business functions and their dependencies. When exam questions reference BIA, connect it to how MTD values are derived and validated.
- The Budget Justification Angle: RPO directly drives infrastructure costs. A security manager uses RPO to justify investment in replication technologies, backup solutions, and recovery sites. Frame your answers around cost-benefit analysis: tighter RPO = higher cost, but potentially lower business impact from data loss.
- Testing and Validation: Paper metrics are meaningless without testing. Exam scenarios often probe whether stated RTOs are achievable. The security manager's role includes ensuring regular DR tests validate that RTO + WRT actually falls within MTD—and updating plans when they don't.
Challenge Yourself
Tough, realistic CISSP scenarios that expose gaps before exam day does.
Take the Challenge
